Cyber Deception - Deception/Canaries/Honey X
- brencronin
- Apr 9, 2025
- 15 min read
Updated: Apr 11, 2025

A honeypot is a 'a container in which honey is kept'. Honeypots should be left for honey!

Rule #1: Don’t Call cyber deception "Honeypots"
The term "honeypot" carries negative connotations that can hinder leadership buy-in and jeopardize your cyber deception project before it even starts. There are two primary concerns:
Attracting Unwanted Threats – The misconception that honeypots invite cybercriminal activity, increasing the risk of attackers breaching containment and infiltrating the organization.
Legal & Ethical Concerns – Some view honeypots as a form of legal entrapment, potentially exposing the organization to civil or legal liability.
While cyber deception can include internet-facing decoys, they are only a small component of a broader cyber deception strategy and are not required for a successful implementation. Avoiding the term "honeypots" ensures broader acceptance of cyber deception initiatives.
Rule #2: Cyber Deception Detects Both External and Internal Threats
Cyber deception is not just about catching external attackers, it’s also a powerful tool for detecting malicious insiders.

At its core, cyber deception involves strategically placing fake credentials, tokens, documents, services, or systems within an environment. These assets should be:
Unused by legitimate users
Highly instrumented to trigger alerts when accessed
Designed to expose unauthorized activity
By setting traps that no normal user should ever access, security teams gain high-fidelity alerts that minimize false positives. Unlike traditional detection methods, which often generate noise, cyber deception signals real malicious intent, making it one of the most effective cybersecurity detection mechanisms available.
Deploying Cyber Deception
Before implementing a cyber deception strategy, start by answering the following questions:
Will you deploy a vendor-based cyber deception solution?
Will you develop an in-house (homegrown) cyber deception solution?
Will you use a combination of both vendor-based and homegrown cyber deception solutions?
Vendor-Based Cyber Deception Solutions
While vendor solutions are not required for a successful cyber deception program, they can significantly influence how you plan and implement your strategy. Many leading cybersecurity vendors now integrate deception capabilities into their broader security platforms. Some notable cyber deception solutions include:
Acalvio
CounterCraft
CyberTrap
Deceptive Bytes
FortiDeceptor
Labyrinth
Lupovis
Microsoft Defender XDR Deception
Proofpoint
RevBits
Thinkst Applied Research
Tracebit
Zscaler
Zscaler Deception
(Cyber deception vendor list primarily taken from Chris Rays 'GigaOm Radar for Deception Technology v4')
Cyber Deception in the Context of Preemptive Cyber Defense
According to Gartner, cyber deception falls under the broader category of Preemptive Cyber Defense, a proactive approach that goes beyond traditional detection and response to prevent attacks before they occur.
Key subcategories under Preemptive Cyber Defense include:
Automated Moving Target Defense (AMTD) – Dynamically shifting attack surfaces to confuse and mislead adversaries.
Threat Simulation & Automated Exposure Management – Continuously testing defenses against potential attack scenarios.
Predictive Threat Intelligence – Using AI-driven insights to anticipate and mitigate threats.
Advanced Cyber Deception – Deploying decoys, fake assets, and deceptive tactics to detect and mislead attackers.
Network Threat Detection & Observability – Gaining deeper visibility into network activities to identify suspicious behavior.
Developing a Cyber Deception Plan
The foundation of any successful cyber deception program begins with a well-structured and deliberate deployment plan. This plan should guide implementation by addressing both technical and procedural considerations, while aligning with the organization’s broader security objectives.
Just like other areas of cybersecurity, cyber deception draws heavily from military concepts and doctrine. Just as concepts like the “Cyber Kill Chain” and “Cyber Kill Web” are rooted in military strategy, the influence of military thinking is especially evident in deception theory.
One key reference in this space is The Art of Deception in Warfare by Colonel Michael Dewar, a classic text that outlines core principles still relevant today in the digital domain.

Dewar’s Principles of Deception (Applied to Cybersecurity)
Centralized Command and Control - Deception efforts must be coordinated. Poorly planned or fragmented strategies can do more harm than good, confusing internal teams or triggering unintended consequences.
Thorough Preparation - Effective deception demands careful planning. This includes intelligence gathering, threat modeling, and scenario-based “wargaming” to anticipate attacker reactions.
Use of Logical Deception Strategies - Deception should follow a rational narrative, whether hiding real assets or presenting false ones. Consistency in the deception story is key to credibility.
Dissimulation (Hiding the Real) - Concealing real systems, behaviors, or data from attackers. Examples: Moving crown-jewel assets out of normal visibility or masking lateral movement paths.
Simulation (Showing the False) - Creating realistic-looking fake systems, credentials, file shares, or users designed to attract and mislead attackers.
Source Corroboration - Deceptive indicators must be distributed across multiple layer, logs, hosts, credentials, and systems. If it's too centralized or “too perfect,” it risks detection by the attacker.
Timing and Tempo - Deceptive artifacts must be discovered naturally over time, providing enough exposure for attackers to engage but not enough to thoroughly analyze or identify as fake.
Operational Security (OPSEC) - Deception cannot appear staged or too convenient. Simultaneously, real assets and intentions must remain well-guarded and free from inadvertent exposure.
There are countless stories from the cyber defender trenches, stories of blue teamers who crafted the perfect deception traps, rubbing their hands together, just waiting to catch those sneaky red teamers. But nope. The red teamers ended up gliding past the deception trap. “Hmm, that account named Admin_RC4_4UOnly seems legit”. LOL In some cases, it’s as simple as this: the deception could have caught the red teamers, but they just never came across it. Either way, there is hope that the cyber deception dialogue becomes a valuable part of the engagement, helping the organization strengthen its defenses, and maybe, just maybe, the blue team’s deceptions will snag the red team next time.

Dewar outlines several core deception techniques, each designed to manipulate perception and decision-making:
Encouraging the Obvious - Reinforce what the target already expects, confirming their assumptions to divert attention from your true objective.
The Lure - Dangle an enticing but unexpected opportunity in front of the target, baiting them into a carefully set trap.
The Repetitive Process - Build trust through repetition. Consistently show one pattern of behavior until the target becomes complacent, then strike with the real action.
The Double Bluff - Tell the truth to a target who assumes deception, betting they’ll dismiss it as part of the ruse.
The Unintentional Mistake - Make it appear that sensitive information was leaked by accident, luring the target into trusting what they’ve “discovered.”
Bad Luck - Exploit the fog of war, make it seem as though the target gained critical intel due to chance or uncontrolled events.
Substitution - Feed false information to establish a belief, then swap it out with the truth (or vice versa) when the timing benefits you most.
Impersonation - Pose as the target, adopting their systems, uniforms, or behaviors to blend in and mislead.
Physical Deception - Use classic sensory tricks like camouflage, concealment, and decoys to manipulate the target’s perception of the physical environment.
The most common cyber deception techniques rely on "showing the false", primarily through the use of lures and decoys, and then monitoring those decoys for interaction. However, the real effectiveness of deception doesn’t just come from the lures and decoys themselves. Success depends on other foundational elements like strategic preparation, careful timing and tempo, source corroboration, and centralized command and control of the deception effort.
A great resource for those interested in going further into cyber deception techniques and planning is the book, Intrusion Detection Honeypots: Detection Through Deception by Chris Sanders. It provides an in-depth look at the methods and mindset behind effective cyber deception planning and implementation.

Key Questions for Cyber Deception Deployment
Although this article doesn't cover full-scale deception planning in depth, here are some key high-level questions that should be considered when designing and implementing an effective cyber deception strategy.
What types of deceptions will you deploy?
Where will the deceptions be located?
How will you lure attackers toward the deception and away from real assets?
How will you make the deception appear authentic?
How will you detect and be alerted when an attacker interacts with the deception?
Popular cyber deception Lures and Decoys include:
Deception Documents – Decoy files containing fake but enticing data.
Deception Systems – Fake endpoints, servers, or services that mimic real infrastructure.
Deception Credentials – Fake user accounts or passwords designed to bait attackers.
Deception Tokens – Injected artifacts like fake API keys, SSH keys, or session cookies.
Cyber Deception Types - Technological and Process Consideration
Technological Fit:
Ensure your deception aligns with the technology your organization actually uses.
Example: Deploying a Programmable Logic Controller (PLC) deception system in a corporate office without industrial controls has little value.
Base your deception deployment on threat modeling, focusing on the systems, credentials, and data that attackers are most likely to target.
Operational Feasibility:
Consider whether your team can effectively deploy and manage the deception.
Some deception tactics require setting up new systems, while others involve injecting deception data (e.g., tokens, credentials) into existing infrastructure.
IT and security administrators may resist deploying deception, fearing potential system impact. Work with them by demonstrating:
How deception credentials lack real privileges and pose no security risk.
How injecting a single fake credential is no different from the many inactive user accounts already present on many systems (a story for another day lol).
Phased Implementation Approach:
Start simple, then expand.
Example: Place a fake password list in an Excel file on SharePoint and monitor login attempts using credentials from that file.
Work with IT teams to gradually introduce deception elements into existing systems.
Placement of Deceptions
Deception placement should align with threat modeling and attack surface analysis:
Think like an attacker – Identify the assets most likely to be targeted.
Example: In a school system, attackers may aim to steal and encrypt student records and systems to perform double extortion (e.g., "Pay or we will release privacy data and pay to recover your systems")
In a data center, attackers may target Industrial Control Systems (ICS) along with traditional ransomware operations. So, PLC deceptions near real PLCs could make sense.
Visibility is key – Deceptions must be placed where attackers will find them.
A well-hidden deception is useless if no attacker interacts with it.
By strategically placing, managing, and phasing in cyber deception tactics, organizations can increase detection fidelity, reduce false positives, and effectively lure attackers into controlled traps.
How will you lure hackers to the deceptions and way from real stuff on your network
Certain techniques make cyber deception significantly more compelling and harder for attackers to resist. Some of the most effective standout methods include:
Enticing Object Names and Metadata – Files and folders crafted with tempting titles (e.g., "2024_Q4_BonusPlan.xlsx") or believable metadata to attract attention while staying contextually relevant.
Credential and Identity Lures – Artifacts like cached credentials, access tokens, or authentication cookies designed to bait attackers into triggering identity-based decoys.
Remote Access Traps – Fake services and file shares. For example, remote services like RDP, VNC, or SSH endpoints that appear misconfigured or under protected, inviting deeper interaction.
Interactive Web Interfaces – Deceptive web portals or admin panels that mimic legitimate internal resources, designed to capture attacker behavior upon access.
How will you sell the deception as real?
Consistency with the Environment
Naming Conventions - Use realistic hostnames, usernames, and file names that match patterns in your real environment (e.g., HR-SERVER02, MJones-FIN, or Confidential_Q3Review.pdf).
Domain Structure - Place decoys in believable locations in the directory tree (e.g., a decoy file under \\HumanResources\shared\Bonuses) and ensure IP/DNS aligns with real subnet allocations.
Recent Activity & Metadata
File Metadata - Modify creation/modification dates and access history to align with typical user behavior.
Browser History & Cache - Populate decoy machines with recent logins, open tabs, or bookmarks to simulate use.
Running Services - Ensure decoys run believable processes and services (e.g., WinWord.exe, Outlook.exe, even dummy Chrome sessions).
Match Operational Tempo and Simulated Errors or Misconfigurations
Tied to Real Events - Roll out a new lures and decoy around the same time as a real IT project (e.g., a system upgrade) to blend in.
Standard IT Admin Oversights: Add deliberate but believable flaws, like a comment in a PowerShell script saying #TODO: remove hardcoded creds before prod.
Log files: Sprinkle logs or plaintext files with fake stack traces or secrets (API_KEY=qwerty-fake-key).
How will you be alerted when something triggers a deception trap?
Detecting interactions with cyber deception assets requires careful planning across two critical areas: the alerting mechanism and the alert data quality. Both are essential for effective incident detection and meaningful analysis.
Deception Alerting Mechanism
Alerting on deception can be tricky, especially when it involves file access or interaction with decoy assets. Traditional methods like auditing file access are notorious for generating noise and require specific audit policies and configurations. This highlights a key balance you must strike:
If your deception is too obvious or too accessible, normal users might accidentally trip alerts causing too many false positives.
If it’s too hidden or too unrealistic, even attackers may ignore it entirely.
You want traps that appear legitimate enough to lure threat actors but are placed in such a way that legitimate users wouldn't encounter them in routine workflows. This is where thoughtful design matters.
It’s also important to think about the operational traceability of these traps. If alerts are firing from multiple decoys and lures across the environment, will you be able to easily trace them back to the specific system or trap that was tripped?

Deception Alert Data Quality
The value of deception isn’t just in generating an alert, it’s in what that alert tells you. Quality deception alert data should go beyond a simple "something happened" and answer deeper questions about the adversary’s behavior. For example:
Credential Use - What credentials did the attacker try to use? Were decoy credentials injected into memory or file systems and later used?
Directory Browsing - What was the attacker trying to find? Did they snoop through sensitive-looking folders or follow paths that mirrored your real infrastructure?
These kinds of insights help defenders build a clearer picture of the threat actor’s intent, tactics, and level of knowledge about the environment.
Interactive Deception Systems
While basic lures and decoys can trigger alerts, full interactive deception platforms, like decoy virtual machines or sandboxed fake environments, offer even richer intelligence. These systems can capture toolsets used by attackers, their command-line behavior, malware downloads, lateral movement attempts, and more.
The trade-off? They require significantly more planning, tuning, and operational upkeep.
Examples of Lures and Decoys and their placement
One of the simplest and most accessible deception techniques is deploying fake documents or password files within commonly accessed document repositories like SharePoint.
Threat actors frequently search for files such as Excel spreadsheets, OneNote files, or text documents that appear to contain sensitive data like usernames and passwords. Placing convincing decoy content in these locations can be a highly effective trap. It’s low-cost, easy to implement, and doesn’t require specialized infrastructure, just the effort of building and maintaining a realistic-looking SharePoint site that mimics genuine business activity.
These lures can take multiple forms:
Credential-based lures - Fake usernames and passwords that, when used, trigger alerts through your SIEM by matching watchlists or authentication rules.
Access-based lures - Real but isolated credentials that provide access to decoy systems, baiting the attacker deeper into a controlled environment where further monitoring and engagement can occur.

To spice things up for realism, you could even place credentials in older versions of OneNote. I have seen in red team engagements, credentials discovered in OneNote notebooks, reported as a finding, and later removed by sysadmins, only for the older OneNote version history to still retain the sensitive credential data. That lingering exposure can also be turned into a highly believable lure, an organization that had weak credentials management and took some steps to clean it up but missed an important loophole in their efforts.
However, there’s an important trade-off: realism vs. visibility. A deception is only valuable if an attacker sees it, but if it's too realistic or deeply hidden, it might never be discovered. The key is placing lures in locations that feel authentic and tempting to threat actors, without making them so obscure that they’re overlooked entirely.
Leveraging Red Team Enumeration Tools to Design Realistic Lures and Decoys
Red team enumeration tools are a goldmine for brainstorming effective lures and decoys, both in terms of placement and realism. A great example is SeatBelt, a popular tool used by red teamers to gather valuable system information during engagements. It collects details such as the EDR in use, logged-in users, browser history, browser credentials, and more.

This same logic can be flipped to enhance your cyber deception strategy. For instance, attackers are often on the lookout for browsing history, saved credentials, or signs of recent user activity. That makes these excellent areas to plant lures. You might seed browser history with visits to decoy systems, or embed decoy credentials within session data. These tactics help mimic real user behavior and can trip attackers who exploit poor identity hygiene.
However, realism matters. If you deploy a decoy system that lacks something as basic as browser history, on a machine that should clearly have some, that gap can blow the deception’s cover. This highlights the need to think like an attacker when planning deceptions: the more plausible your traps, the more likely they’ll catch someone.
Deception Products Examples
Microsoft Defender for Endpoint – Deception Technology: Lures & Decoys
Microsoft Defender for Endpoint (MDE) leverages deception technology through Lures and Decoys to proactively detect attacker behavior. These elements are deployed directly through the Defender EDR agent on enrolled devices.
Lures: Digital breadcrumbs (e.g., file paths, documents, or credentials) placed on endpoints to attract and guide attackers toward decoys. They mimic real assets to increase believability.
Decoys: Fake user accounts or host systems that don’t exist in Active Directory or Azure AD. When attackers interact with these decoys, an alert is triggered, exposing malicious activity.
All decoys are deployed locally on MDE-enrolled endpoints — not in Active Directory or Azure AD.

Types of Lures
Microsoft Defender supports two types of lures within its deception framework:
Basic Lures
Non-interactive artifacts like fake documents or shortcut files
Minimal or no integration with the actual environment
Simple traps to test for surface-level threat engagement
Advanced Lures
Interactive elements such as cached credentials and Active Directory responses
Integrated with environment context to simulate realistic attack surfaces
For example, injected decoy credentials that respond to LDAP queries or authentication attempts

Deception Rules and Scope
Deception is configured through deception rules that define what lures and decoys are deployed and where. The scope setting is critical, especially in sensitive environments.
You can target deception to:
All Windows client devices
Specific device groups or tags
Best Practice: Avoid deploying lures or decoys on executive or privileged devices unless intentionally creating lures and decoys on high-value target systems.

Decoy Deployment Process
During setup, Defender XDR auto-generates decoys based on your environment:
Fake users and hosts are created using detected naming conventions
These do not exist in your actual directory services
Optionally, you can define Custom IP-based Decoys, such as sandboxed machines or honeypots, for advanced threat detection

Lure Deployment Options
You have two main options when configuring lures:
Use auto-generated lures (default and recommended for basic coverage)
Use custom lures only (for environments requiring tighter control and specificity)

Alerting on Deception Triggers
When an attacker engages with deception elements, Defender generates specific alerts marked with a “Deceptive” tag. Examples include:
Sign-in attempt with a deceptive user account
Connection attempt to a deceptive host
Each alert includes:
The Deception tag for easy filtering
The name of the decoy asset (user or host)
The attack method, such as lateral movement or unauthorized login attempts

Zscaler – Deception Technology
In 2021, Zscaler acquired the cyber deception startup Smokescreen.io, which now forms the foundation of Zscaler’s deception technology platform. This platform can be deployed as a standalone solution or as a licensed add-on for existing Zscaler Private Access (ZPA) and Zscaler Internet Access (ZIA) customers.
Deployment is streamlined through the existing Zscaler Client Connector (ZCC) agent, which organizations running ZIA or ZPA already have installed. The ZCC agent plays a key role in enforcing Zero Trust Network Access (ZTNA), managing secure connectivity to both internet resources via ZIA and internal applications via ZPA.
The diagram below illustrates how the ZCC agent integrates with Zscaler services to provide secure, segmented ZTNA access.
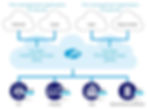
Zero Trust Network Access (ZTNA) is a robust security approach that verifies every user and device before granting access to applications and data, regardless of their location. Instead of assuming trust based solely on network membership, ZTNA enforces access according to strict policies that limit exposure to only specific resources. For example, Zscaler Private Access (ZPA) securely connects authorized systems to applications hosted in data centers or the cloud without exposing them to the public internet, ensuring only permitted users and devices gain access.

Building on the strength of Zscaler Private Access (ZPA), Zscaler’s deception platform adds a powerful overlay that leverages the existing ZPA infrastructure and Zscaler Client Connector (ZCC) agents. This integration enables seamless deployment of decoys within a dedicated Deception Cloud. Through the ZCC agent, organizations can configure deceptive element, such as landmine decoys, fake credentials, files, processes, and lures that point to other decoys on endpoints. These strategically placed traps divert adversaries away from real assets and toward instrumented decoy applications designed for monitoring and alerting, giving defenders early warning and valuable insights.

Zscaler Deception Capabilities Overview
Zscaler currently offers two deception modules: Deception Standard and Deception Advanced. As expected, the Advanced tier comes at a higher cost but unlocks enhanced functionality. This includes a broader variety of decoys and lures, deeper integrations (e.g., SIEM alerting), and advanced workflows such as firewall integrations and automated response options.
With Zscaler Deception, you can configure and deploy a wide range of decoy types, including:
Endpoint Decoys (Landmine Decoys) - These are strategically placed fake files, credentials, and application lures on endpoints. They're designed to appear enticing and legitimate to attackers, increasing the chances of interaction and triggering alerts.
Network Decoys - These simulate real network services and protocols, including:
Web (HTTP/HTTPS)
Shared drives
FTP, SSH, Telnet
Windows services
Databases (MySQL, PostgreSQL, MongoDB)
IoT/SCADA protocols (AMQP, MQTT)
Custom services and Docker containers
AI-generated content to enhance believability
Active Directory (AD) Decoys - These include decoy service and privileged accounts that mimic real users, configured to detect techniques like Kerberoasting, brute force, and privilege escalation. As with other AD deception approaches, these require scripts to be run within the environment to deploy the decoy objects effectively.
Cloud Decoys - Cloud deception allows for the creation of decoy resources within public cloud environments. These assets mimic legitimate cloud resources and can be deployed after integrating your cloud platform with Zscaler Deception.
Threat Intelligence (TI) Decoys - These are interactive, internet-facing decoys designed to detect reconnaissance and attack attempts targeting public-facing assets. They provide valuable threat intel and early warnings of malicious activity.
To make decoys more scalable and realistic, Zscaler also offers MirageMaker, a toolkit packed with datasets and customization options to ensure that your decoys blend seamlessly into the environment.
Maximizing Coverage: Bridging Gaps in Agent-Based Cyber Deception
As shown in the examples, organizations already running security agents, such as ZTNA or EDR, are well-positioned to enhance their defenses with cyber deception as a strategic add-on. This approach can significantly improve detection capabilities without the overhead of deploying “YACS” (Yet Another Cyber System).
However, there are still gaps to consider. Many organizations don’t have ZTNA or EDR agents deployed across all devices. Even in mature environments, limitations may exist due to unsupported platforms (e.g., specialized appliances) or architectural constraints.
To address these blind spots, organizations should consider augmenting their cyber deception strategy with additional methods, targeting high-risk areas not covered by traditional agents, to ensure comprehensive protection across the full attack surface.
References
Gigaoam cyber deception report:
Book: The Art of Deception in Warfare:
Book: Intrusion Detection Honeypots:
Catching red teams with honeypots part 1: local recon:
Counter Craft Cyber Deception:
SeatBelt:
Active Directory Certificate Service (ADCS) Honeypot:
Microsoft Defender Deception:
Zscaler ZPA:
Zscaler deception:
FortiDeceptor:
A comprehensive survey on cyber deception techniques to improve honeypot performance:
List of Honeypot projects:
Canary Tools: