WELCOME TO CRONINITY
 |  |  |
|---|---|---|
 |  |  |
Adversary-in-the-Middle (AiTM) and Business Email Compromise (BEC)
Cyberattacks persistently target both systems and individuals. Among these, compromising user credentials stands out as a prevalent...
Malware Analysis - Encoding/Decoding to Mask/Unmask Hackers Dirty Deeds - Base64
One critical aspect of malware behavior lies in Data Obfuscation, where malware seeks to conceal its activities through various...
Incident Response (IR) Exercises
Incident Response (IR) Exercise Phases Establish Exercise Interval and Planning timelines: First, establish the IR exercise execution...
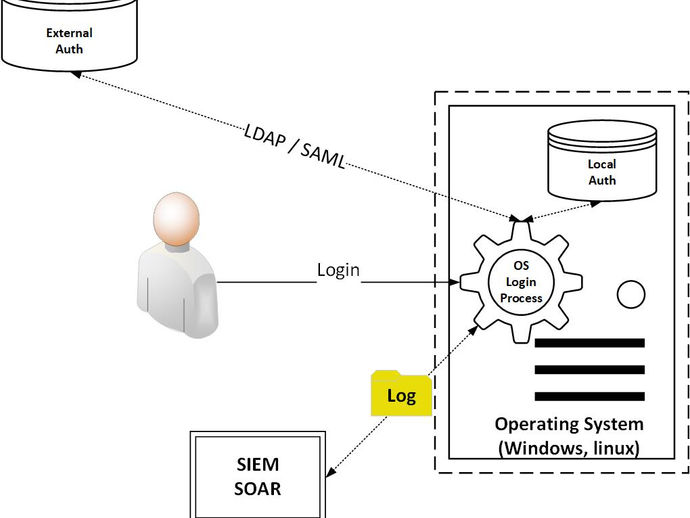
Connecting Logs to Identities in devices and Applications
Authentication Logging for Operating Systems Overview One crucial aspect of cybersecurity involves monitoring logins associated with user...
Cyber Threat Intelligence (CTI) and its many faces - Foundational Threat Indicator Lookup Services & Threat Indicator Feeds
Cyber Threat Intelligence (CTI) plays a vital role in enhancing detection capabilities and empowering organizations to make well-informed...
Network Detection & Response (NDR) - Zeek 'Alerting' - Odd Remote Access Behavior and Tools
When collecting Zeek data, you have a rich source of information for analysis. However, when monitoring systems, it's crucial to...
Elastic Security - Random Notes and Links
Elastic - Overview When considering data storage in Elasticsearch, it's common to think of relational databases. However, Elasticsearch...
Logging Systems - Logging Ain't Easy But it's Necessary
NIST 800-53 logging controls are primarily categorized within the AU (Audit and Accountability) control family. Within AU, there are...
Cybersecurity Logging Systems - C.E.S 'Crowdstrike, Elastic, Splunk'
In cybersecurity, various logging systems are employed, often known as 'Security Information & Event Management' (SIEM) systems when...
Ransomware - Techniques - Encryption via GPUpdate
Ensuring the security of an organization's Domain Controller (DC) is paramount, recognizing it as a critical asset that must be protected...
Agentless Integration of IDS/IPS and Vulnerability Data
Intrusion Detection/Protection Systems (IDS/IPS) examine network traffic using rules and signatures. Some of these rules or signatures...
The Cybersecurity Suri
In the realm of cybersecurity, there is also a 'Suri,' which is the abbreviation for Suricata. Suricata stands as an open-source,...
Vulnerability Management - Fragile Scanning
Certain devices are considered 'fragile' where aggressive vulnerability scanning could have a risk of impacting the availability of the...
Vulnerability Management - Tracking & Treating
In a previous article I highlighted a framework for vulnerability management program, developed by SANS instructors Jonathan Risto and...
Vulnerability Management - Vulnerability Prioritization
In a prior article, I introduced a vulnerability management program framework known as P.I.A.C.T., developed by SANS instructors Jonathan...
Management - Performance Goals
Managing people can be tough. One of the pillars of successful management is leading employees to meet the organizations objectives and...
Vulnerability Management - The Homonymy of "Scanning"
One of the most frequently used terms in cybersecurity is "Scanning." However, this term can encompass various meanings within the...
Cybersecurity Metrics
Metrics are the lifeblood of business decision-making, cherished by executives who rely on them to steer their organizations toward...